xchat forging replies to non-existent messages pic.twitter.com/Tm2ieS3AjY
— SELO (@seloesque) December 15, 2025
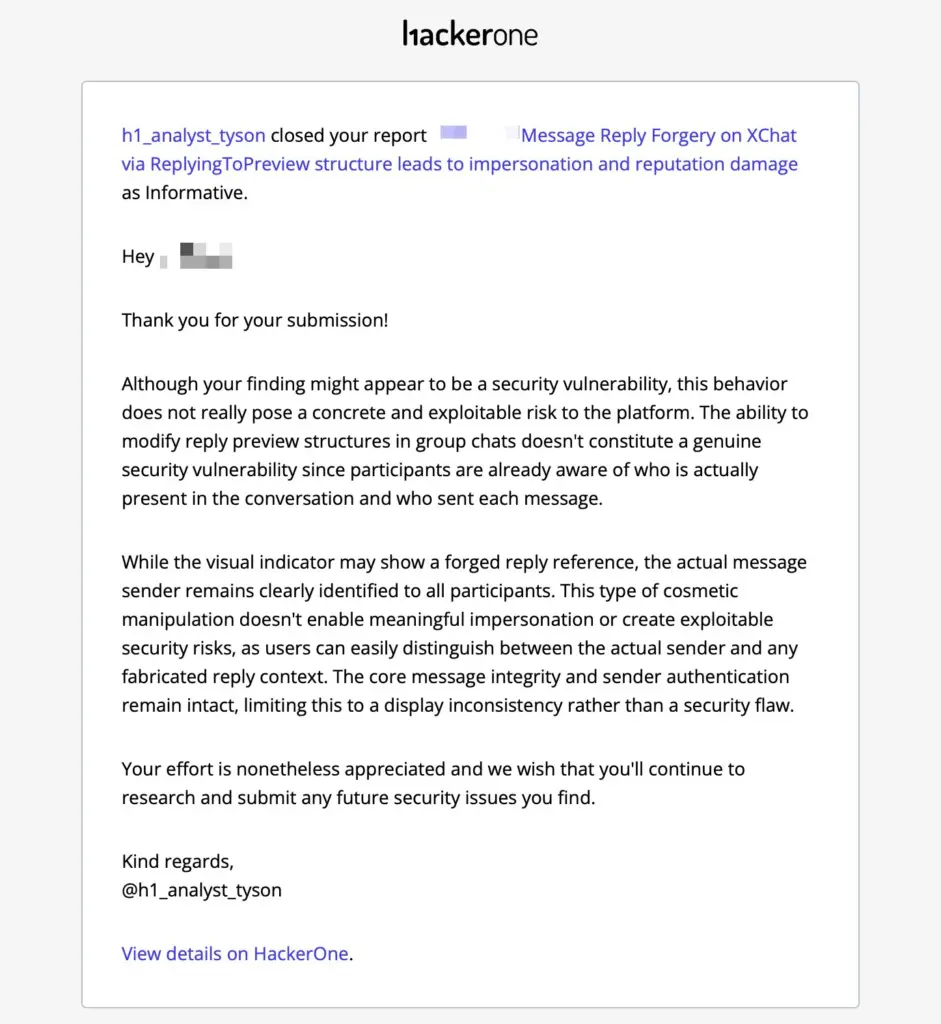
Update 17/12/25 – 12:44 pm (IST): The situation took a confusing turn when SELO revealed that HackerOne had initially closed the report as “Informative,” dismissing the exploit as a mere “display inconsistency” rather than a security flaw.
However, following that public disclosure, X engineering lead Mike (@cambridgemike) stepped in to contradict the rejection. He assured the researcher that the team has actually been treating the issue as a “top priority” since it was reported and is now actively looking into the HackerOne submission.
Original article published on December 16, 2025, follows:
A developer and security researcher known as SELO has uncovered a startling vulnerability in X’s messaging infrastructure, specifically within group chats. The flaw effectively allows users to forge replies to messages that never existed.
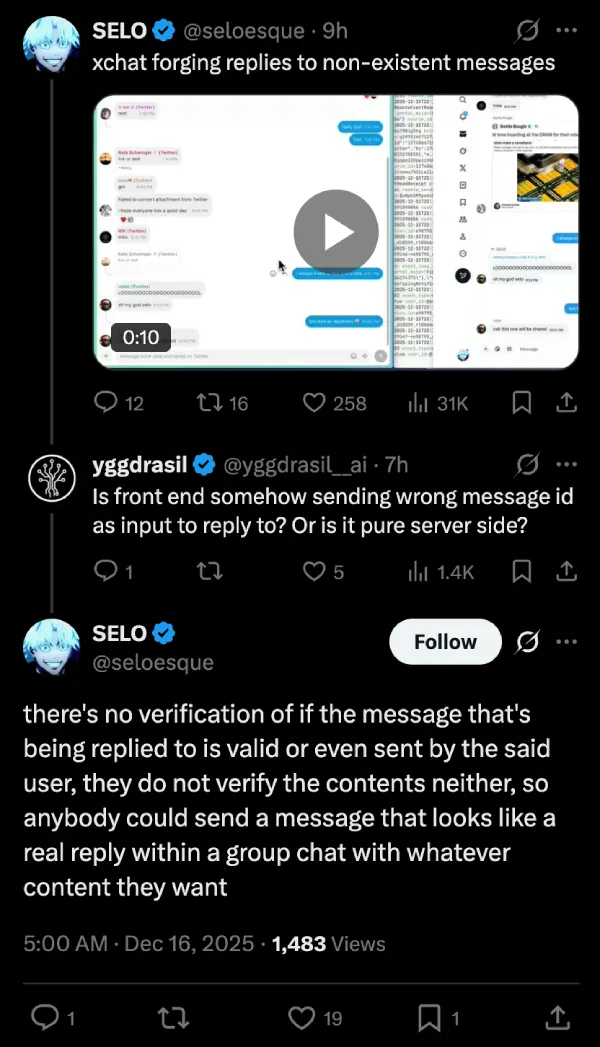
This isn’t just a UI glitch where a message looks funny on your own screen. According to the proof-of-concept video shared by the developer, the exploit allows an attacker to inject a reply that references a fake message, making it appear to everyone in the chat as if a specific user said something they absolutely did not.
In the video shared on X, we see a script running alongside the chat interface. The script executes, and suddenly, reply bubbles appear in the conversation thread quoting “original” messages that aren’t actually there. For this demo, SELO makes it seem like the replies are to messages from “Elon Musk” and “Nikita Bier,” even though obviously neither of the two had any messages. This creates a seamless illusion of a conversation that never happened.
When asked if this was a client-side issue, SELO clarified that the problem lies deeper.
“There’s no verification of if the message that’s being replied to is valid or even sent by the said user,” SELO explained. “They do not verify the contents neither, so anybody could send a message that looks like a real reply within a group chat with whatever content they want.”
This is a massive oversight in how the platform handles message IDs. In a secure messaging environment, the server should validate that the message ID being replied to actually exists and matches the content being quoted. X apparently skips this step entirely.
It’s worth noting that we are familiar with SELO’s work. We recently covered how X shut down XGlobalRank, another project by the same developer that aimed to bring transparency to the platform’s ranking system. It seems they have a knack for poking holes in Elon Musk’s app.
The implications here are genuinely concerning. As one user pointed out in the replies, this is the “perfect tool for some serious gaslighting.”
While some users are jokingly asking for the script to “stir up trouble,” others are rightly pointing out that this highlights significant gaps in the engineering team’s QA process.
X has not yet officially acknowledged the flaw. However, given the severity of a bug that undermines the basic trust of private communication, we expect a patch — or at least a server-side hotfix — to roll out very soon.
Until then, if you see a screenshot of a DM or a group chat reply that looks suspicious, take it with a massive grain of salt. The message you’re looking at might literally be a ghost.