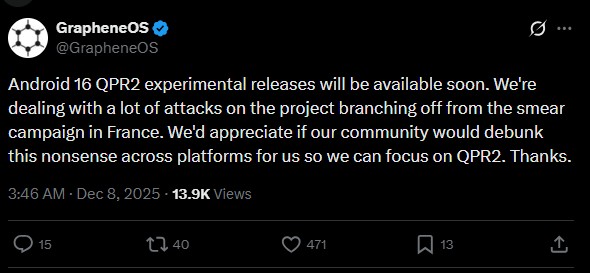
GrapheneOS is gearing up for its next major milestone, announcing that Android 16 QPR2 experimental releases will be available soon. However, the announcement comes with a heavy caveat: the privacy-focused project is currently battling what it describes as a continued “smear campaign” stemming from recent conflicts in France.
The developers have issued a call to action to their community, asking users to help “debunk this nonsense” so the team can focus on the technical development of QPR2. This plea follows a particularly sensational allegation from a user claiming that a failure in GrapheneOS security features led to their charge for premeditated murder.
For those following the saga, GrapheneOS has had a tumultuous few weeks in Europe. Late last month, we reported on GrapheneOS pulling its servers from France following accusations of sabotage by competitors and threats from authorities. This coincided with a media narrative in the region branding the OS as the “criminal’s choice” after police reportedly struggled to crack Pixel devices running the software.
Despite the team pushing forward with experimental support for the Pixel 10 series, the backlash hasn’t subsided.
The murder charge allegation
The latest controversy gaining traction in forums and X (formerly Twitter) involves a user, handle @b8r200, who alleges that Belgian police successfully cracked their GrapheneOS device, leading to severe legal consequences.
The user shared an image of an alleged police summons from the Antwerp Police in Belgium. The document invites the recipient for an interrogation regarding premeditated murder for events occurring in July 2024.
You can view the document shared by the user below:

The user’s narrative is highly specific and damaging to the project’s reputation. According to @b8r200, they utilized a specific GrapheneOS security feature designed to format the device upon entry of a “duress password.” The user claims that when the situation arose, the feature failed to execute the wipe.
“I have a warrant because @GrapheneOS failed me. Your features clearly failed,” the user captioned the image. “The basis of my claim is simple: I used the correct duress password, the device was configured properly, and the outcome after the fact did not match what the feature is supposed to do.”
The user further elaborated on the consequences of this alleged technical failure:
“The escalation to premeditated murder happened after the device was in the hands of the Specialized Research Service (DGO/DRA). The information used to upgrade the charge exists only on the device.”
In a parallel discussion on the GrapheneOS forum, the user offered more context, stating: “Basically, I was suspected of a murder… My OS was seized, I had all security features enabled. Now I got a call from my lawyer saying I have a warrant for my arrest… the warrant was sent out by the INTEL department of the federal police.”
GrapheneOS responds: User error or forensic tools?
The GrapheneOS team has strongly pushed back against these claims. While acknowledging the user’s legal trouble, they dispute the technical failure of the OS. The developers suggested that if the device was accessed, it was likely due to user-side weaknesses rather than a broken duress feature.
In their response, the team noted that the situation was likely caused by an easily guessable lock method, biometrics without 2FA, or not updated device.
It is a known reality in digital forensics that no OS is magic; if a user utilizes a weak PIN (like 123456) or has an outdated security patch, commercial tools like Cellebrite or GrayKey can potentially brute-force entry. GrapheneOS also reiterated that they cannot make absolute promises regarding the capabilities of state-level commercial cracking tools if the user’s security hygiene is poor.
The GrapheneOS community has rallied around the developers, with many dismissing the user’s claims as “bait” or part of the aforementioned smear campaign. The forum thread discussing the incident has exploded with over 180 replies, with experienced users pointing out that a duress password failure is highly unlikely if configured correctly, and questioning the veracity of the user’s story.
GrapheneOS views this as an attempt to “neuter” the project by sowing discord. They are counting on their loyal userbase to fact-check these claims while they turn their attention back to code.
Despite the drama, development continues. The Android 16 QPR2 experimental releases are imminent. As the project faces increased scrutiny from both authorities and detractors, the team is clearly hoping the software’s performance will speak louder than the current wave of allegations.
We will continue to monitor the situation and update you when the QPR2 release goes live.