A significant security flaw in the DuckDuckGo Privacy Browser for Android could have allowed attackers to steal sensitive user data, including saved passwords and bookmarks. The vulnerability, now identified as CVE-2025-48464, was discovered by security engineer Kang Hao Leo and detailed in a recent blog post. It affects users on Android 13 and older versions of the operating system.
The attack targets DuckDuckGo’s Sync & Backup feature, which lets you synchronize your browsing data (like bookmarks and passwords) across different devices without needing an account. To make this work, DuckDuckGo provides you with a “Recovery PDF.” This document contains a unique QR code and a recovery key that acts as the master password for your synced data. The browser advises users to keep this file safe, as anyone who has it can access all their synced information.
The vulnerability discovered by Leo created a loophole that could allow a malicious app to steal this exact Recovery PDF directly from the DuckDuckGo browser’s private storage.
The exploit required a user to perform two actions:
- Install a malicious app on their phone.
- Visit a malicious website using the DuckDuckGo browser.
The attack unfolds in a clever, two-step process. The malicious website contains a special type of link known as an intent:// URL. Think of this not as a regular link to a webpage, but as a command that tells your phone to perform an action or open an app. In this case, the link was crafted to command the DuckDuckGo browser to do something it shouldn’t: take its own sensitive “Recovery PDF” and send it to the malicious app.
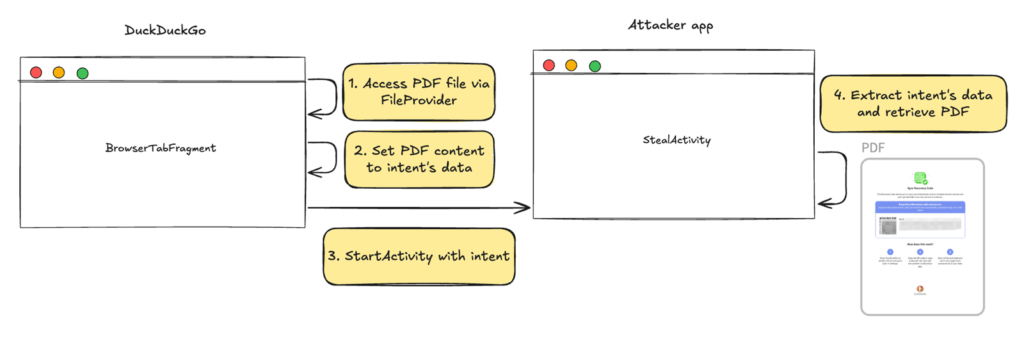
Normally, Android’s security model prevents one app from simply stealing files from another. However, Leo discovered that a quirk in Android 13 and earlier created a critical oversight. When DuckDuckGo processed this malicious “command link,” the old Android system would automatically and temporarily grant the malicious app permission to read the file. The browser was essentially tricked into handing over the keys to the kingdom.
The researcher explained that this happened because older Android versions automatically added a critical permission flag (FLAG_GRANT_READ_URI_PERMISSION) to intents that contained text, a loophole that attackers could exploit. This “magic” behavior does not exist in Android 14 and newer, which is why they are not affected.
This is why keeping both your apps and your phone’s operating system up-to-date is so important. While DuckDuckGo is known for its strong focus on privacy, this vulnerability shows how even secure apps can be compromised by underlying issues in an outdated OS.
The flaw isn’t just in the app but in how the app interacts with an older, less secure version of Android. As the researcher behind the discovery put it, “those [OS] patches are what keep your apps and devices from being outdated – and exploited. So the next time your phone begs for an update… It’s not being needy, it’s protecting you.”
If you’re using the DuckDuckGo browser on Android 13 and older versions, you should ensure the app is updated to the latest version via the Google Play Store. Furthermore, if your device supports it, updating your phone to the latest version of Android is one of the best steps you can take to protect yourself from a wide range of security threats.



