New updates are being added at the bottom of this story…….
In older days of Android, hardware assisted encryption was not readily available. Due to performance constraints, the userdata section of the phone was kept unencrypted (i.e. easy game for law enforcement agencies and rogue users).

With the introduction of Android 5.0 Lollipop, Google decided to turn on encryption by default. Initially phones faced some hiccups to cope up with the extra overhead, but eventually hardware vendors started to ship encryption accelerators.
Since the release of Android 7.0 Nougat, the OS supports file-based encryption (FBE) besides the legacy full-disk encryption (FDE). The concerned keys are derived from a secure area of the SoC, called the TrustZone.
A Trusted Execution Environment (TEE) is a secure area inside a main processor. It runs in parallel of the operating system, in an isolated environment. It guarantees that the code and data loaded in the TEE are protected with respect to confidentiality and integrity. This alongside-system is intended to be more secure than the classic system (called REE or Rich Execution Environment) by using both hardware and software to protect data and code.
(Source)
Major Android version updates often require updating the underlying firmware components, which include the TrustZone (TZ) as well. As a matter of fact, the same thing happened with OnePlus 3/3T Android Pie update with some twist.
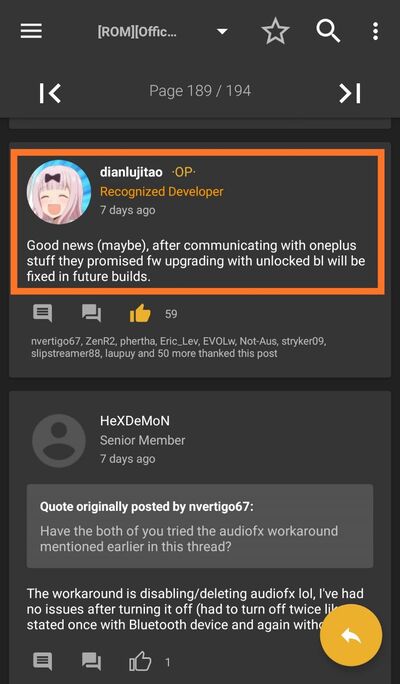
I’m quoting XDA recognized developer dianlujitao here:
If your data is encrypted and bootloader is unlocked, after upgrading to Pie modem firmware, there’s 100% chance of your data to become corrupted, and probably no way to restore them. The cause is on firmware side, probably something wrong with key migration, so there’s no way for 3rd party developers to fix it.
The bug is present since the closed beta builds of OxygenOS/HydrogenOS 9.0. OnePlus officials were notified about the situation, and they were supposedly aware of the issue.
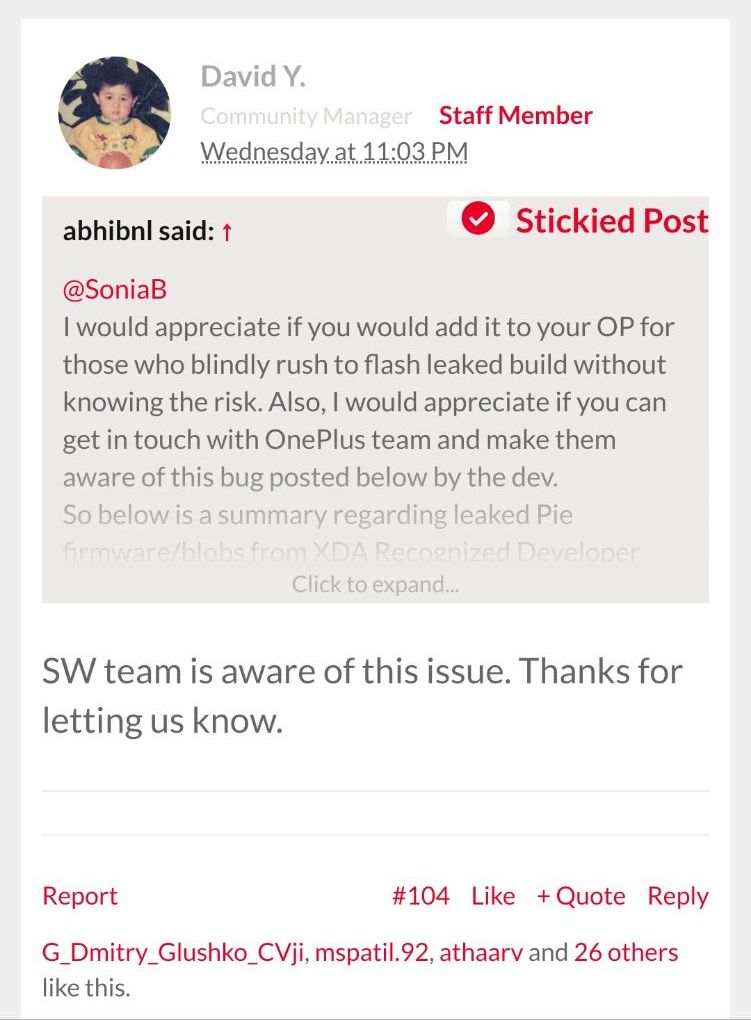
Rather than fixing the actual reason, OnePlus team published two sets of public beta builds of the Android Pie update for the OnePlus 3T and 3, with a strict requirement of having a locked bootloader.
Thanks to the immense popularity of the OnePlus phones and their developer friendliness, a lot of users unlocked the bootloader of their phones to try out mods and custom developments.
Given the circumstances, data corruption for having an unlocked bootloader is not at all a decent way when it comes to software designing.
I couldn’t comprehend why do they apply diverse low-level strategies to locked and unlocked bootloader. Arguably this is a bug and should be fixed when they started rolling OTA updates to the public, but it’s also possible that this is by design and aims to restrict “unsafe” operations. Regardless, always be careful and backup your data before upgrading firmware in the near future.
-dianlujitao
The Chinese OEM is gradually rolling out the final stable version of Android Pie update for OnePlus 3 and 3T in the form of OxygenOS 9.0.2 since yesterday. The official announcement doesn’t contain any kind of warning related to the status of the bootloader.
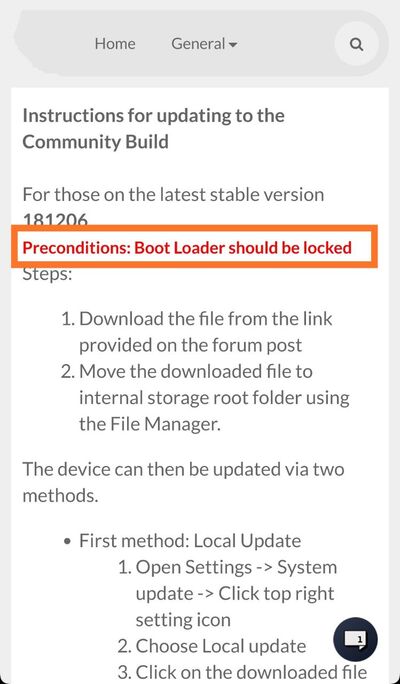
However, the bug is still at large – even in the final OTA update – as several OnePlus 3/3T users are facing data corruption issue when updating from last stable version of OxygenOS (5.0.8, based on Android 8.0 Oreo).
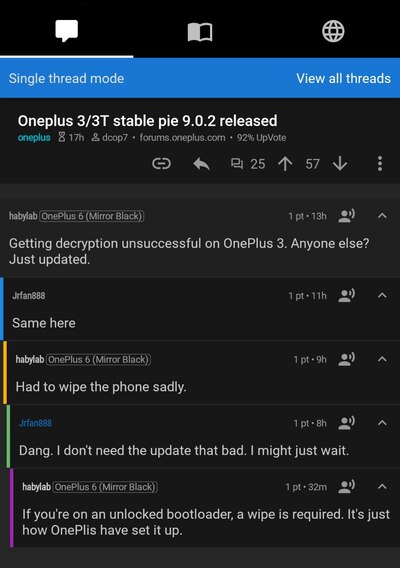
hey guys, I tried flashing using oxygen updater, the phone displays decryption error and twrp is still there, any ideas onwhat should i do now?
(Source)
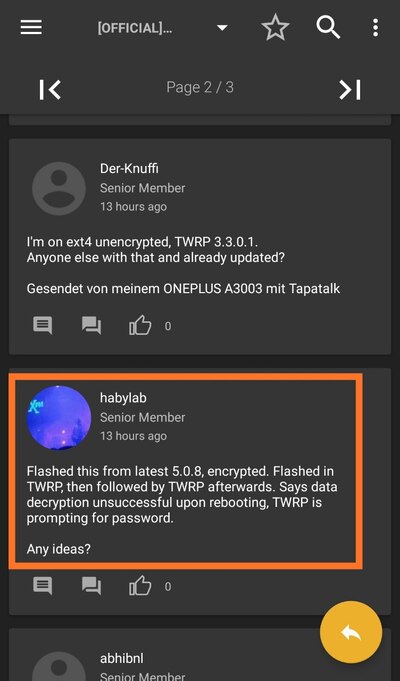
The Oxygen Updater team decided to put a warning for regular users about the potential data decryption bug on unlocked bootloader.
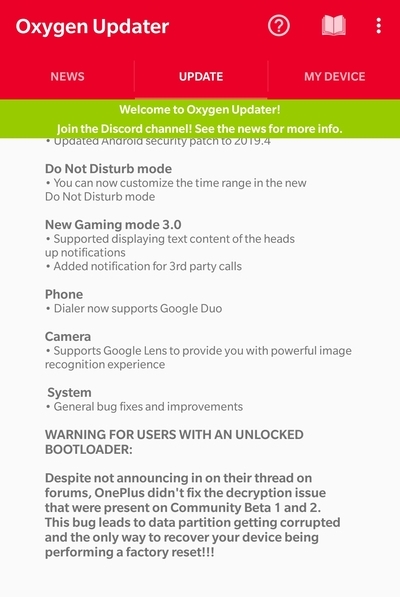
Those who are already on Community Beta (CB) builds of OxygenOS 9.0 should be unaffected by the glitch, as the underlying firmware has already been updated for them. But the majority of the OnePlus 3/3T users are on the verge of getting their data corrupted.
dianlujitao was in touch with the OnePlus engineers, and got assurance about fixing the bug as soon as possible. Guess they were not able to cover every test cases.
Considering the gravity of the situation, PiunikaWeb is trying to contact OnePlus for a statement. Stay tuned for further update. Meanwhile, do backup everything (including files in your internal storage) before installing the Pie update for OnePlus 3T/3.
Update (June 8)
OnePlus 3/3T users are now getting OxygenOS 9.0.3 update, which fixes the Parallel WhatsApp crashing bug. However, the data corruption issue still exists.
PiunikaWeb is a unique initiative that mainly focuses on investigative journalism. This means we do a lot of hard work to come up with news stories that are either ‘exclusive,’ ‘breaking,’ or ‘curated’ in nature. Perhaps that’s the reason our work has been picked by the likes of Forbes, Foxnews, Gizmodo, TechCrunch, Engadget, The Verge, Macrumors, and more. Do take a tour of our website to get a feel of our work. And if you like what we do, stay connected with us on Twitter (@PiunikaWeb) and other social media channels to receive timely updates on stories we publish.

![[9.0.3 too] OnePlus 3/3T Android Pie update: Data decryption issue on unlocked bootloader still present in OxygenOS 9.0.2 [9.0.3 too] OnePlus 3/3T Android Pie update: Data decryption issue on unlocked bootloader still present in OxygenOS 9.0.2](https://piunikaweb.com/wp-content/uploads/2019/05/facepalm_cain-statue_banner.jpg)

